ISO 27001 Training & Awareness
Train your key people about ISO 27001 requirements and provide company-wide cybersecurity awareness training to all of your employees.
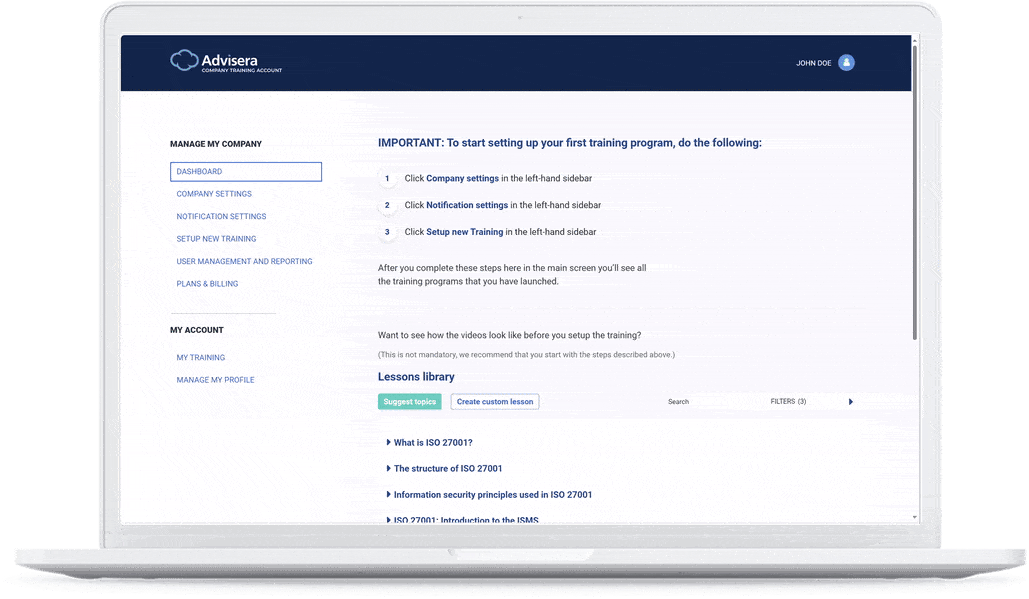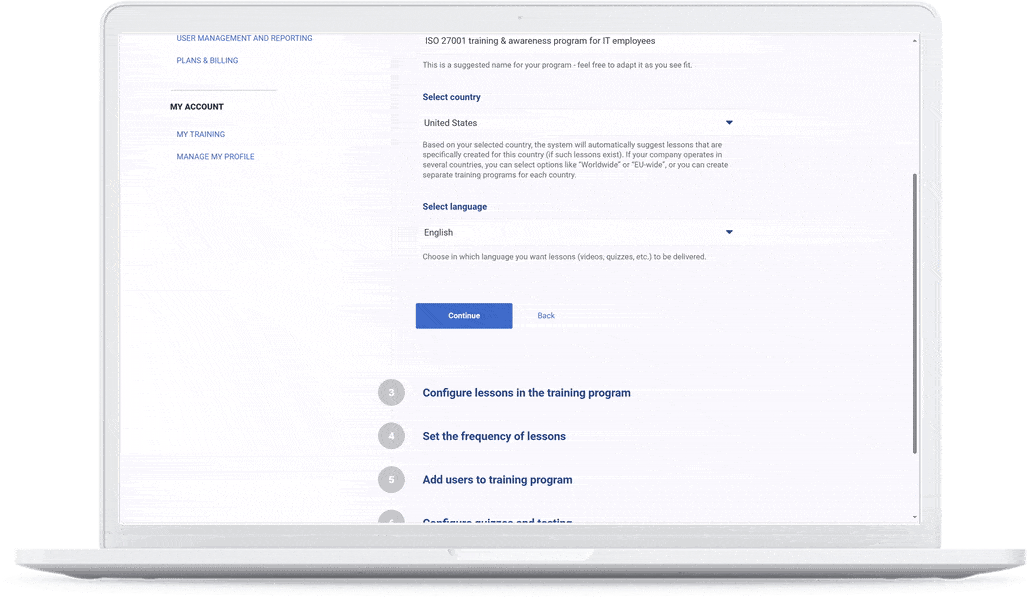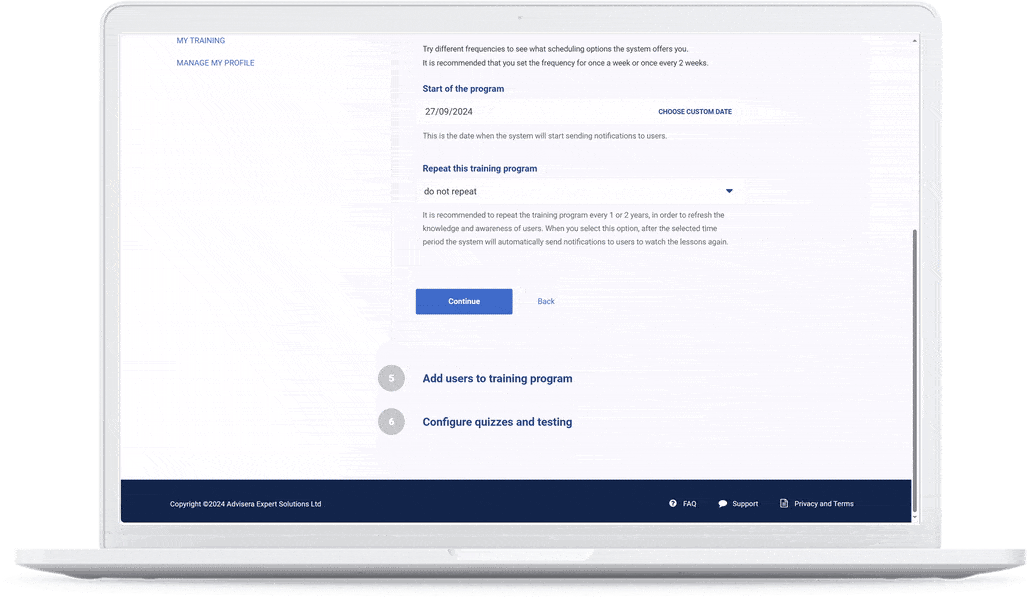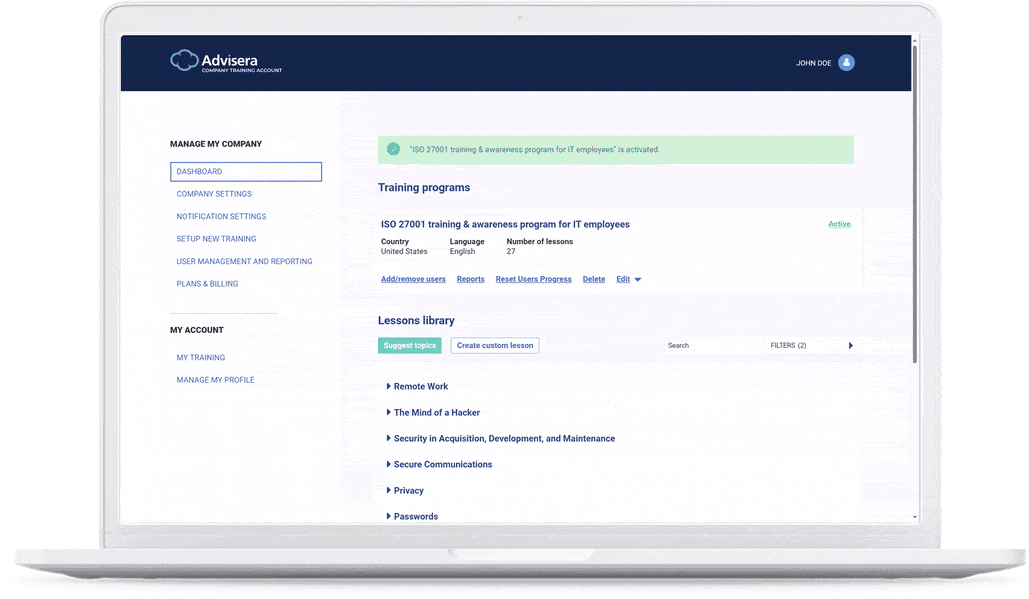
The quickest route to company-wide training
A set of 100 videos that explain all aspects of ISO 27001, and cover all key topics for cybersecurity hygiene — configure the whole training & awareness program in a couple of minutes, and enable each employee to watch videos on their devices.
On the left-hand side, you can see one of the videos from the ISO 27001 Training & Awareness available in Advisera’s Company Training Academy.
ISO 27001 lessons library
- What is ISO 27001? (1:02)
Learn about the basics of the leading cybersecurity standardWhole ISO 27001
- The structure of ISO 27001 (2:01)
ISO 27001 main clauses and their purposeWhole ISO 27001
- Information security principles used in ISO 27001 (2:07)
An example of confidentiality, integrity, and availability in practiceWhole ISO 27001
- ISO 27001: Introduction to the ISMS (2:22)
The purpose of an Information Security Management SystemWhole ISO 27001
- Key roles in ISO 27001 implementation (1:07)
Roles of the project manager, security officer, and senior managementWhole ISO 27001
- Documenting ISO 27001 requirements (2:55)
Mandatory and non-mandatory documentsWhole ISO 27001
- Implementing ISO 27001 requirements (2:13)
Using the PDCA cycle as guidance for implementationWhole ISO 27001
- ISO 27001 Benefits (2:02)
4 key benefits: compliance, marketing, costs, and better organizationWhole ISO 27001
- ISO 27001: Understanding your organization and its context (2:03)
Analyzing internal and external issuesISO 27001 clause 4.1
- ISO 27001: Understanding the needs and expectations of interested parties (1:35)
Who are interested parties, and what are their requirements?ISO 27001 clause 4.2
- ISO 27001: Determining the scope of the ISMS (1:50)
What is the ISMS scope, and why is it important?ISO 27001 clause 4.3
- ISO 27001: Leadership and commitment (1:45)
Key senior management activities that represent commitmentISO 27001 clause 5.1
- ISO 27001: Information Security Policy (1:13)
Mandatory elements of this top-level policyISO 27001 clause 5.2
- ISO 27001: Organizational roles, responsibilities, and authorities (2:14)
Which roles are mandatory according to ISO 27001?ISO 27001 clause 5.3
- ISO 27001: Information security objectives (2:14)
Why are objectives important, and how to define them?ISO 27001 clause 6.2
- ISO 27001: Resources (1:40)
Example of resources and how to document themISO 27001 clause 7.1
- ISO 27001: Competence (1:22)
The options to acquire required skills and knowledgeISO 27001 clause 7.2
- ISO 27001: Awareness (1:23)
How to organize security awareness in a companyISO 27001 clause 7.3
- ISO 27001: Communication (1:24)
What kind of communication is required, and why is it important?ISO 27001 clause 7.4
- ISO 27001: Documented information (3:12)
Creating, updating, and controlling policies, procedures, and recordsISO 27001 clause 7.5
- ISO 27001: Addressing risks and opportunities (1:46)
The basics of risk managementISO 27001 clause 6.1.1
- ISO 27001: Risk management process (2:15)
Five key steps to assess and treat risksISO 27001 clause 6.1.2, ISO 27001 clause 6.1.3
- ISO 27001: Information security risk assessment – Risk identification (3:03)
Risk identification, risk analysis, and risk evaluationISO 27001 clause 6.1.2
- ISO 27001: Information security risk assessment – Risk analysis and evaluation (2:40)
Using scales to assess impact and likelihoodSO 27001 clause 6.1.2
- ISO 27001: Information security risk treatment (0:00)
Four most common options for treating risksISO 27001 clause 6.1.3
- ISO 27001: Statement of Applicability (1:59)
The purpose and structure of the SoAISO 27001 clause 6.1.3
- ISO 27001: Formulating the risk treatment plan (1:49)
The purpose and mandatory elements of the RTPISO 27001 clause 6.1.3
- ISO 27001: Implementing the risk treatment plan (1:15)
Key elements of implementation and how to document resultsISO 27001 clause 8.3
- ISO 27001: Operational planning and control (2:18)
Key elements of the Do phase in the PDCA cycleISO 27001 clause 8.1
- ISO 27001: Operating the ISMS (1:18)
What does operating the ISMS mean?ISO 27001 clause 8
- ISO 27001: Managing outsourcing of operations (1:57)
Examples of security controls for outsourcing activitiesISO 27001 clause 8.1
- ISO 27001: Controlling changes (1:58)
An example of a change management procedureISO 27001 clause 8.1
- ISO 27001: Risk assessment review (1:46)
Why is risk review important, and how often to perform it?ISO 27001 clause 8.2
- ISO 27001: Monitoring, measurement, analysis, and evaluation (3:13)
Key elements for evaluating the performance of the ISMSISO 27001 clause 9.1
- ISO 27001: Internal audit (2:35)
Key elements of an internal auditISO 27001 clause 9.2
- ISO 27001: Management review (2:30)
Inputs and outputs for the management review meetingISO 27001 clause 9.3
- ISO 27001: Nonconformities and corrective actions (3:22)
Required actions when a nonconformity occursISO 27001 clause 10.2
- ISO 27001: Continual improvement (2:19)
Examples of improvement initiativesISO 27001 clause 10.2
- ISO 27001: Introduction to Annex A (5:18)
The purpose and structure of Annex AISO 27001 Annex A
- ISO 27001: People controls (2:05)
Overview of Annex A.6 – Controls before, during, and after employmentISO 27001 Annex A section A.6
- ISO 27001: Physical controls (3:37)
Overview of Annex A.7 – Securing physical areas and equipmentISO 27001 Annex A section A.7
- ISO 27001: Technological controls – overview and new controls (4:13)
Overview of Annex A section A.8 – Technological controlsISO 27001 Annex A section A.8
- ISO 27001: Technological controls – software development (2:51)
Controls that cover architecture, lifecycle, testing, and coding principlesISO 27001 Annex A section A.8
- ISO 27001: Organizational controls – operational security (2:43)
Controls for access control, information transfer, operating procedures, etc.ISO 27001 Annex A section A.5
- ISO 27001: Organizational controls – policies and responsibilities (3:22)
Controls for roles, segregation of duties, contact with external parties, etc.ISO 27001 Annex A section A.5
- ISO 27001: Organizational controls – information and asset management (1:52)
Controls for asset inventory, acceptable use, classification, etc.ISO 27001 Annex A section A.5
- ISO 27001: Technological controls – operational security (4:48)
Controls that cover security in day-to-day IT activitiesISO 27001 Annex A section A.8
- ISO 27001: Organizational controls – supplier security (3:14)
Controls for assessing risks, contractual requirements, monitoring, etc.ISO 27001 Annex A section A.5
- ISO 27001: Organizational controls – incidents and business continuity (4:52)
Controls to deal with threats, events, incidents, and larger disruptionsISO 27001 Annex A section A.5
- ISO 27001: Organizational controls - compliance, privacy, and legal aspects of security (2:49)
Controls that ensure security is compliant with legal requirementsISO 27001 Annex A section A.5
General Cybersecurity lessons library
- Remote Work (4:37)
Risks when working outside of office premisesNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.5.10, A.6.7, A.7.8, A.7.9
- The Mind of a Hacker (5:42)
3 types of hackers and how to protect yourselfNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.6.3
- Security in Acquisition, Development, and Maintenance (12:15)
Cybersecurity in the IT system lifecycleNIS 2 article 21 paragraph 2 point (e), ISO 27001 controls A.8.25, A.8.26, A.8.27, A.8.28, A.8.29, A.8.30, A.8.31, A.8.33
- Secure Communications (13:32)
Securing voice, video, and text communication channelsNIS 2 article 21 paragraph 2 point (j), ISO 27001 controls A.8.20, A.8.21
- Privacy (4:36)
8 privacy principles everyone should knowNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.5.33, A.5.34
- Passwords (5:30)
Creating and keeping passwords secureNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.5.17
- Social Media (5:24)
Main cyber risks when using Facebook, X, LinkedIn, and othersNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.5.10, A.5.14
- Protecting Paperwork (6:35)
Vulnerabilities of paper media, and methods of protecting itNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.5.10, A.5.33, A.7.5, A.7.7
- Basic Cyber Hygiene Practices (4:47)
Essential cybersecurity measures for every userNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.5.10, A.8.1
- Handling Cybersecurity Incidents (6:16)
How to spot and react promptly to cybersecurity concernsNIS 2 article 21 paragraph 2 point (b), ISO 27001 controls A.5.24, A.5.25, A.5.26
- Backup Basics (4:36)
Recovery from data lossNIS 2 article 21 paragraph 2 point (c), ISO 27001 control A.8.13
- Business Continuity (9:40)
Resilience and recovery arrangementsNIS 2 article 21 paragraph 2 point (c), ISO 27001 controls A.5.29, A.5.30, A.8.13, A.8.14
- Basics of Authentication (6:05)
Preventing unauthorized access to digital assetsNIS 2 article 21 paragraph 2 point (j), ISO 27001 control A.8.5
- Disaster Recovery (8:38)
How to recover information systems and dataNIS 2 article 21 paragraph 2 point (c), ISO 27001 control A.5.30, A.8.14
- Cryptography (10:39)
Cryptographic concepts and their applicationNIS 2 article 21 paragraph 2 point (h), ISO 27001 control A.8.24
- Access Control (6:07)
Permitting appropriate access and preventing inappropriate accessNIS 2 article 21 paragraph 2 point (i), ISO 27001 controls A.5.15, A.5.16, A.5.17, A.5.18, A.8.2, A.8.3, A.8.4, A.8.5
- Basics of Network Security (6:43)
Securing digital networks and data communicationsNIS 2 article 21 paragraph 2, ISO 27001 control A.8.20
- Cyber Asset Management (7:22)
Identifying, classifying, securing, and exploiting digital assetsNIS 2 article 21 paragraph 2 point (i), ISO 27001 controls A.5.9
- Emergency Communications (6:30)
Setting up alternative communication methodsNIS 2 article 21 paragraph 2 point (j), ISO 27001 clause 7.4 and controls A.5.14, A.8.14
- Cybersecurity Training and Awareness (11:33)
Creating a program for continuous training and awarenessNIS 2 article 20 paragraph 2, article 21 paragraph 2 point (i), ISO 27001 clauses 7.2, 7.3; control A.6.3
- Information Risk Management (8:29)
Risk assessment and treatment as a foundation of cybersecurityNIS 2 article 20 paragraph 1, article 21 paragraph 1, paragraph 2 point (a), ISO 27001 clauses 6.1, 8.2, 8.3
- Assessing Supplier Security (12:46)
Supplier vulnerabilities, quality, and secure developmentNIS 2 article 21 paragraph 2 point (d), paragraph 3, ISO 27001 controls A.5.19, A.5.20, A.5.21, A.5.22
- Human Resources Security (12:57)
Activities before, during, and after employmentNIS 2 article 21 paragraph 2 point (i), ISO 27001 clauses 7.2, 7.3; controls A.6.1, A.6.2, A.6.3, A.6.4, A.6.5
- Measuring Cybersecurity (7:59)
Assessing the effectiveness of risk managementNIS 2 Article 20 paragraph 1, Article 21 paragraph 2 point (f), ISO 27001 clause 9.1
- Corrective Actions (8:02)
How to eliminate the cause of nonconformitiesNIS 2 article 21 paragraph 4, ISO 27001 clause 10.2
- Management’s Role in Cybersecurity (7:34)
Tasks for senior and mid-level managementNIS 2 article 20 paragraph 1, ISO 27001 clause 5.1
- Insider Threats (6:30)
Managing insiders with access to sensitive informationNIS 2 article 21 paragraph 2 point (i), ISO 27001 controls A.5.15, A.5.33, A.5.35, A.6.1, A.8.2, A.8.16
- Cloud Security Basics (5:38)
Securing data when using cloud servicesNIS 2 article 21 paragraph 2 point (d), ISO 27001 controls A.5.23
- Computer Malware (4:58)
Phishing, ransomware, and spywareNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.8.7
- Email Security (4:08)
Risks related to the usage of emailNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.5.14
- Human Error (4:33)
Reducing mistakes with sensitive informationNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.6.3
- Identity Theft (4:58)
How do cybercriminals steal your identity?NIS 2 article 21 paragraph 2 points (i) and (j), ISO 27001 controls A.5.16, A.5.17, A.8.5
- Device Physical Security (5:52)
Physically securing information and devicesNIS 2 article 21 paragraph 2 point (g), ISO 27001 controls A.7.5, A.7.8, A.7.9, A.7.10, A.8.1
- Intellectual Property (5:36)
Technical, legal, and organizational methods of protecting IPRNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.5.32
- Security of Mobile Devices (5:30)
Protecting laptops, tablets, smartphones, and other devicesNIS 2 article 21 paragraph 2 points (g) and (j), ISO 27001 controls A.5.10, A.5.17, A.6.7, A.7.8, A.7.9, A.7.10, A.8.1, A.8.5, A.8.7
- Social Engineering (6:02)
The most common methods criminals are using to access your accountNIS 2 article 21 paragraph 2 point (g), ISO 27001 control A.5.10
- Managing Supplier Security (6:32)
Risks related to vendors and contractors, and how to handle themNIS 2 article 21 paragraph 2 point (d), ISO 27001 controls A.5.19, A.5.20, A.5.21, A.5.22, A.5.23
Training adjustable for different audiences
Instead of showing the same videos to everyone, you can configure the system so that senior management will see only the videos appropriate for them, IT employees will see different videos, the rest of the employees something else, etc.
Advisera’s Company Training Academy will suggest the most appropriate videos for different audiences, but you’re in control — you define who gets to see what.

Automate training delivery and tracking
You don’t have to torture yourself with organizing a live training that lasts longer than anyone wants to attend. Instead, use Advisera’s Company Training Academy to define how often employees need to watch videos, automatically send email invitations to watch them, track who watched each video, send reminders, and create attendance reports for audit purposes.
Thousands of Successful Customers
Made for easy learning
Let’s face it — people don’t have time to learn about cybersecurity, and most have a hard time understanding techy or lawyer language.
This is why our videos are between 2 and 10 minutes long, and our ISO 27001 experts explain the topics using easy-to-understand language.
Several languages available
We’re translating the videos into all major languages so that any employee in your company can easily understand them.
Besides English, we have videos in German, French, Italian, Dutch, Spanish, Portuguese, Croatian, and we’re adding more.
Custom-made videos
Do you have specific cybersecurity policies or procedures that you’d like to present in a video? No problem! As part of selected plans, we can create custom videos exclusively for your company — personalization has never been easier.
You can also upload the videos you created to complement Advisera’s training videos.


Upload Your Own Training Materials
You can upload your own materials and turn them into engaging lessons. Combine your company’s internal documents, videos, or policies with Advisera’s learning system to build a personalized training experience for your employees.
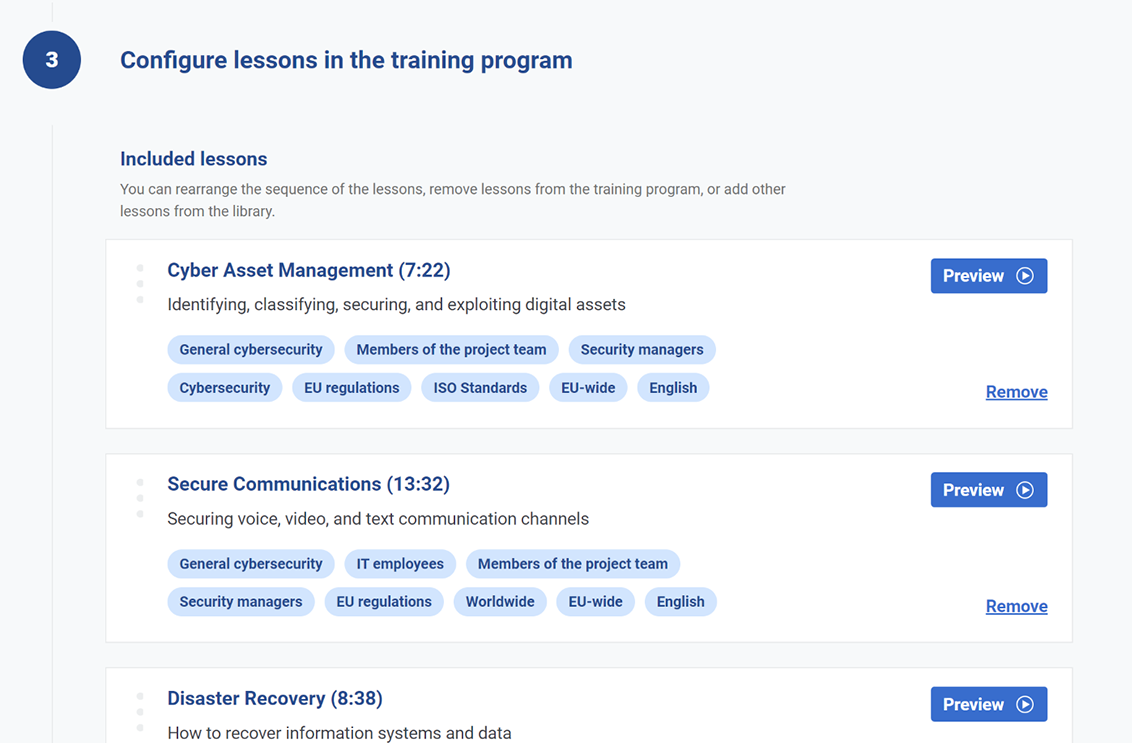
For all use cases
Do you want to organize initial cybersecurity training for your project team? Or do you want regular, continuous training for your whole workforce? Or perhaps onboarding for new employees?
With the Company Training Academy, you can cover all of these cases by setting up separate training programs.
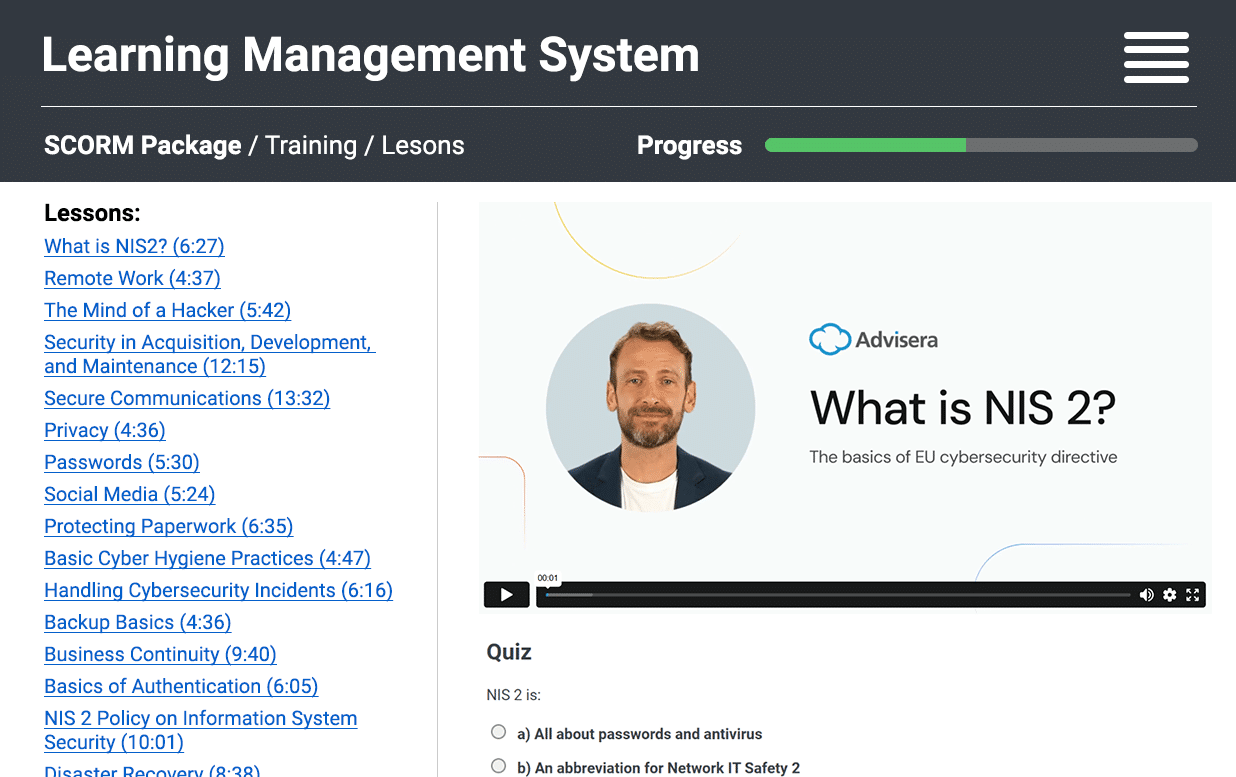
SCORM compatibility for your LMS
Use our training videos in your own learning management system (LMS) — all lessons are available as SCORM packages, including videos, quizzes, and progress tracking. Stay in control while delivering content through your existing platform.
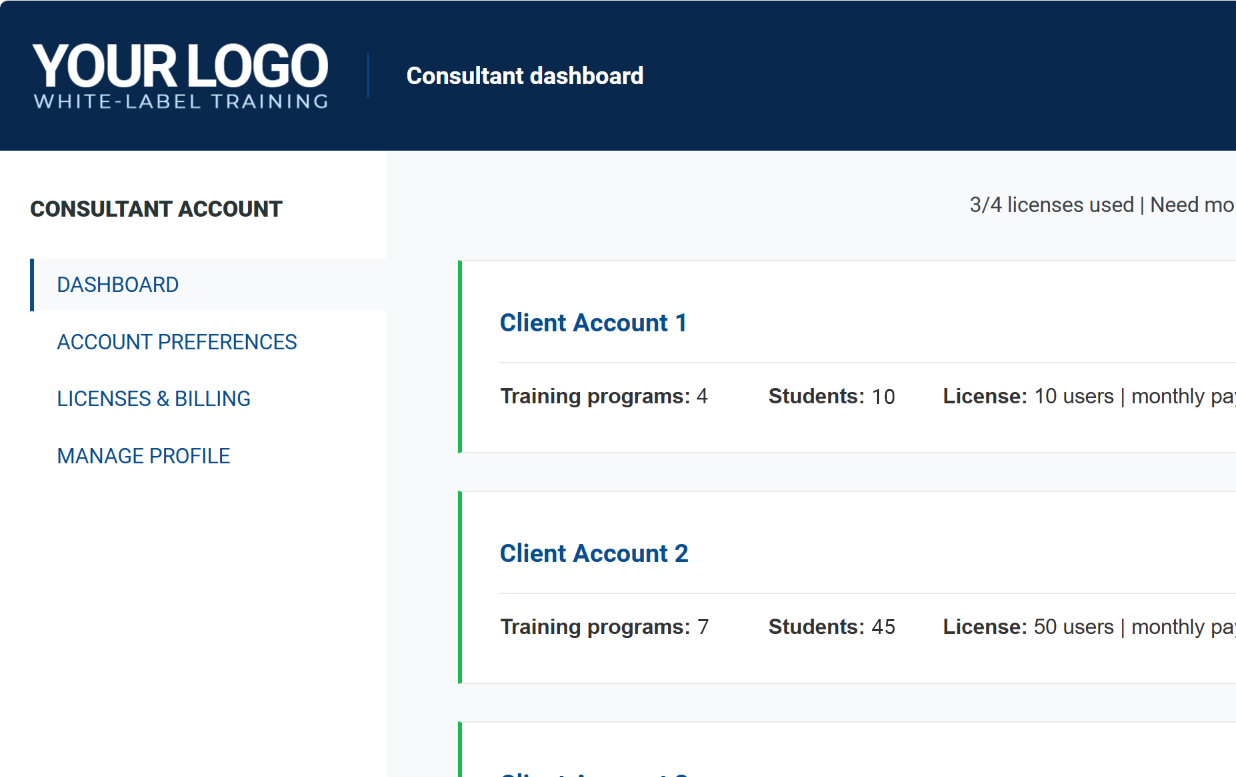
White-label platform for consultants
Grow your business by offering branded cybersecurity and compliance training to your clients. With Advisera’s platform, you can set up and manage training programs for multiple clients — all from one dashboard.
Monthly plan 10 users included
€14
/ month
$15
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 25 users included
€28
/ month
$29
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 50 users included
€56
/ month
$59
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 100 users included
€95
/ month
$99
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 200 users included
€189
/ month
$199
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 300 users included
€285
/ month
$299
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 400 users included
€380
/ month
$399
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 500 users included
€475
/ month
$499
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available only in yearly plan)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 10 users included
€154
/ year
$162
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 25 users included
€298
/ year
$313
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 50 users included
€605
/ year
$637
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 100 users included
€1016
/ year
$1069
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
1 video per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 200 users included
€2042
/ year
$2149
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
2 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 300 users included
€3068
/ year
$3229
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
3 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 400 users included
€4094
/ year
$4309
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
4 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 500 users included
€5120
/ year
$5389
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
5 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
1 training per year
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Contact us for pricing
Custom number of users
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
For all company sizes, all industries
All videos were created to be relevant for small, medium, and large companies, and also for all industries — no matter if your company is a small SaaS provider or a large water utility, your employees will find these videos very appropriate.
In other words, any company implementing and maintaining their ISO 27001 ISMS will find these videos to be the right fit.
Frequently Asked Questions
What is the Company Training Academy?
The Company Training Academy is a company-wide cybersecurity training platform that enables you to configure various training and awareness programs for your entire workforce for, e.g., NIS2, DORA, ISO 27001, GDPR, ISO 42001, security awareness, etc.
How long does it take to set up company-wide training and awareness?
Opening a client account takes less than a minute. The wizard will then guide you through the process of setting up your first training and awareness program, which usually takes 5–10 minutes.
How does the free trial work?
During the 14-day free trial, you will get access to all training & awareness videos, but you will be limited to 10 users. Some more advanced features will be accessible when you upgrade your account. No credit card required.
What forms of payment do you accept?
We accept payment via any major credit or debit card; for a larger number of users, you can pay via wire transfer from your bank account.
How does the Company Training Academy compare to Advisera’s courses?
Advisera’s courses are intended for individuals who want to get in-depth knowledge about a particular framework, while the Company Training Academy is intended for companies that want to automate training and awareness for all of their employees, and track their progress.
Which standards and regulations are covered in the Company Training Academy videos?
Currently, the videos cover NIS2, DORA, ISO 27001, GDPR, ISO 42001, and cybersecurity awareness training.
We’re working on adding videos for other standards and regulations.
Are videos available in languages other than English?
Besides English, we currently have videos in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian. We are working on adding more languages at the moment; please contact us to learn about available languages.
Can we use these videos in our own Learning Management System (LMS)?
Yes. Our training is available as SCORM packages, including videos, quizzes, and progress tracking, for easy integration into your Learning Management System (LMS) – contact us to request the SCORM packages.
Can I upload our own materials to the Company Training Academy?
Yes. You can upload your company’s own training materials and create lessons from them. Supported formats include documents (PDF, DOCX, PPTX, XLSX, etc.), videos (YouTube, Vimeo), and text-based lessons you can create directly in the editor.
Is there a time limit for attending the training?
No, your users can spend as much time as they like attending the lessons, as long as your subscription is active.
What will the users need to access the lessons?
Your users can access the lessons using PC, Mac, or mobile devices, using any major browser (e.g., Chrome, Mozilla, Edge, Safari); a broadband Internet link will also be needed.
What is the format of the training, and how long does it take?
The lessons are a combination of video lectures, quizzes, and test questions. The average time needed per lesson is between 5 and 10 minutes. You can configure your training program to include only a couple of lessons, or several dozen lessons.
What prior knowledge is needed to attend the training?
None. The lessons are created in such a way that a beginner can easily understand them. They are very easy to follow for any type of employees — senior or mid-level management, non-IT employees, tech people, etc.
How can I upgrade my account if I need more users?
Simply click the purchase button for the required number of users in the pricing table, and, after the payment is processed, your Company Training Academy will be upgraded automatically.
Please make sure you use the same email address that you use for your existing account, because it is the only way this process can be done automatically. If you decide to make the purchase with a different email address, make sure you contact our support at support@advisera.com so we can upgrade your account manually.
Is it necessary to purchase training and awareness certificates?
No — you can use a Company Training Academy without purchasing certificates.
There are so many videos — how will I find what is the most appropriate for us?
The Company Training Academy will suggest the most appropriate videos based on the framework you’re interested in (e.g., NIS2), and based on your audience (e.g., senior management).
Further, you can filter all the videos in the Library by country, language, relevant clauses and articles of the framework, and other criteria.
Schedule a Demo
Want our expert to walk you through the product? Schedule a short call. We respond quickly.
