Company Training Academy
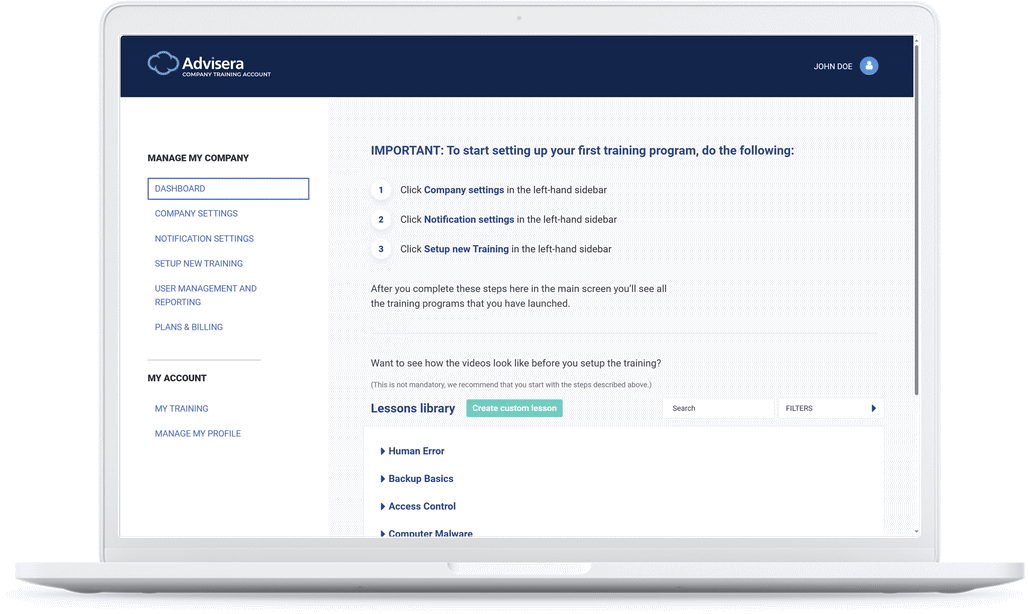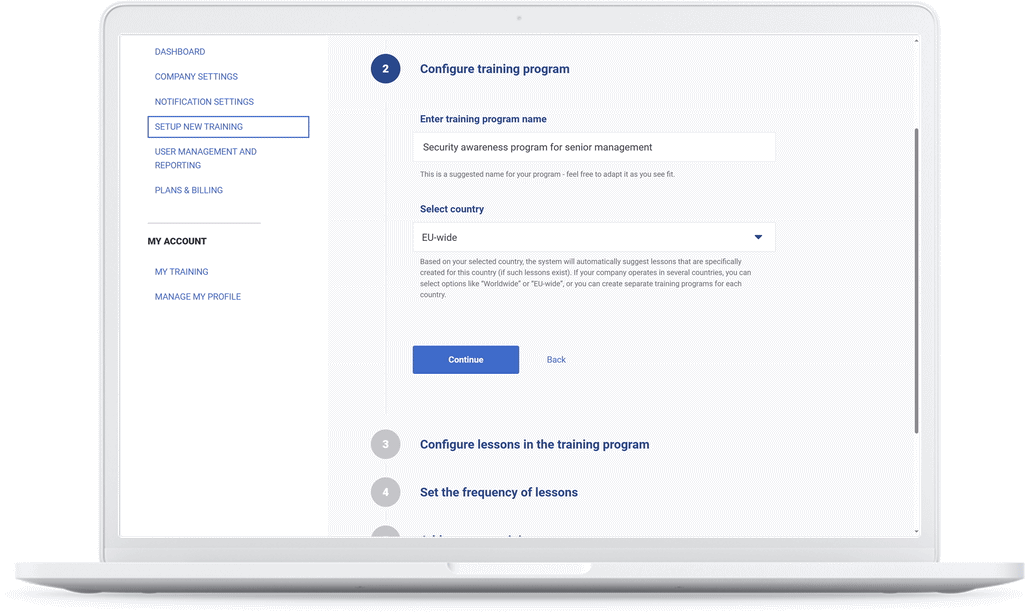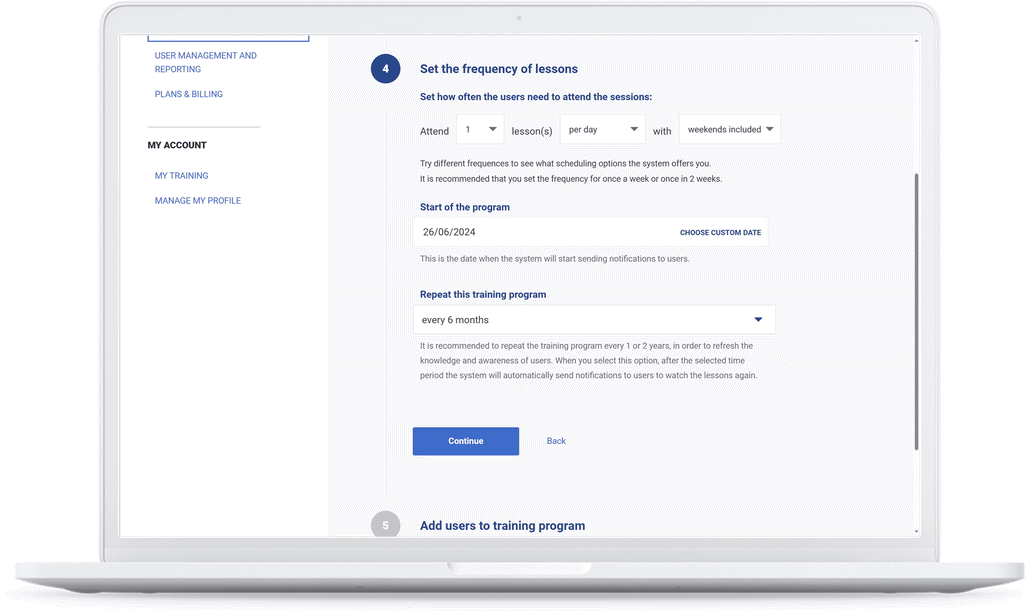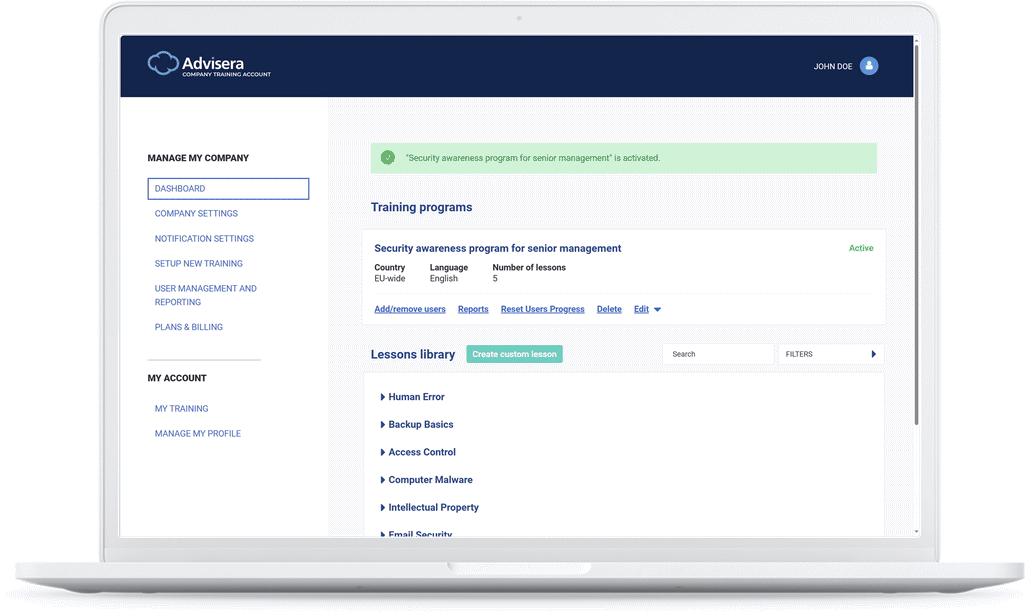
The quickest route to a company-wide training program
Training adjustable for different audiences
Automate training delivery and tracking
Thousands of Successful Customers
Made for easy learning
Several languages available
Country-specific videos


Custom-made videos
For all use cases
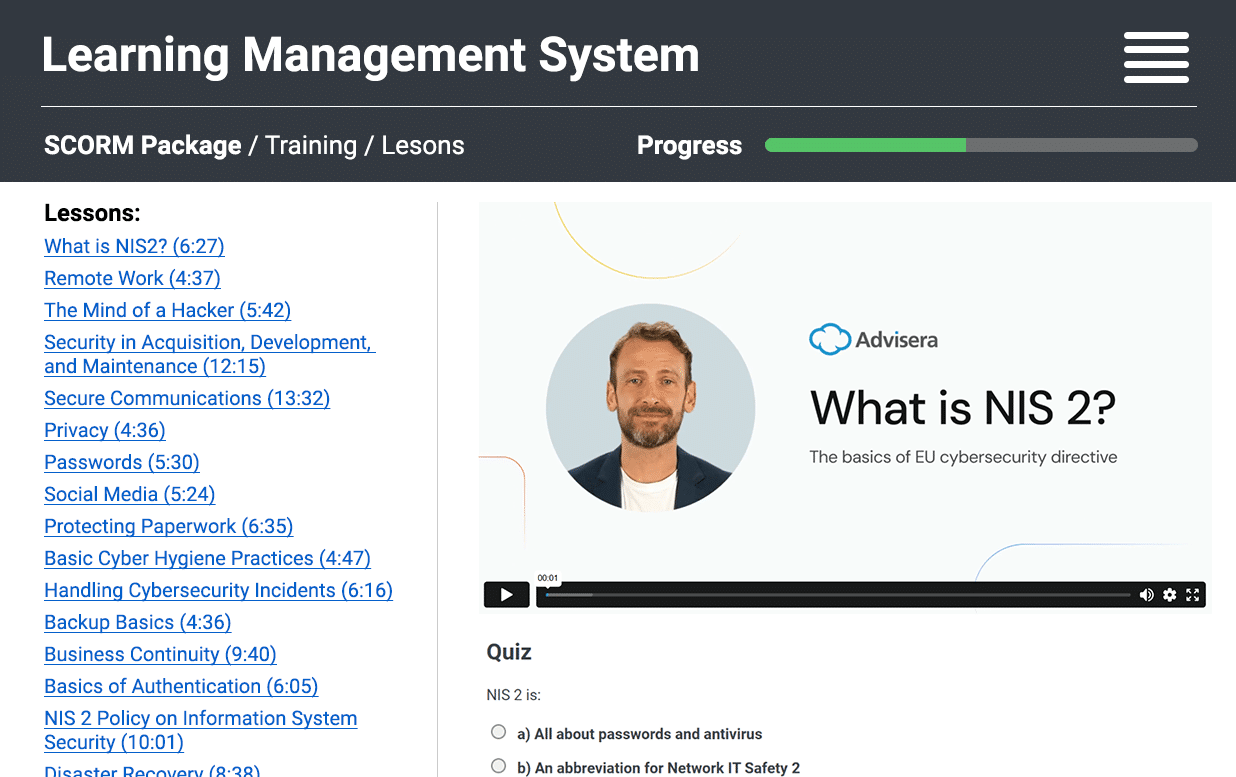
SCORM compatibility for your LMS
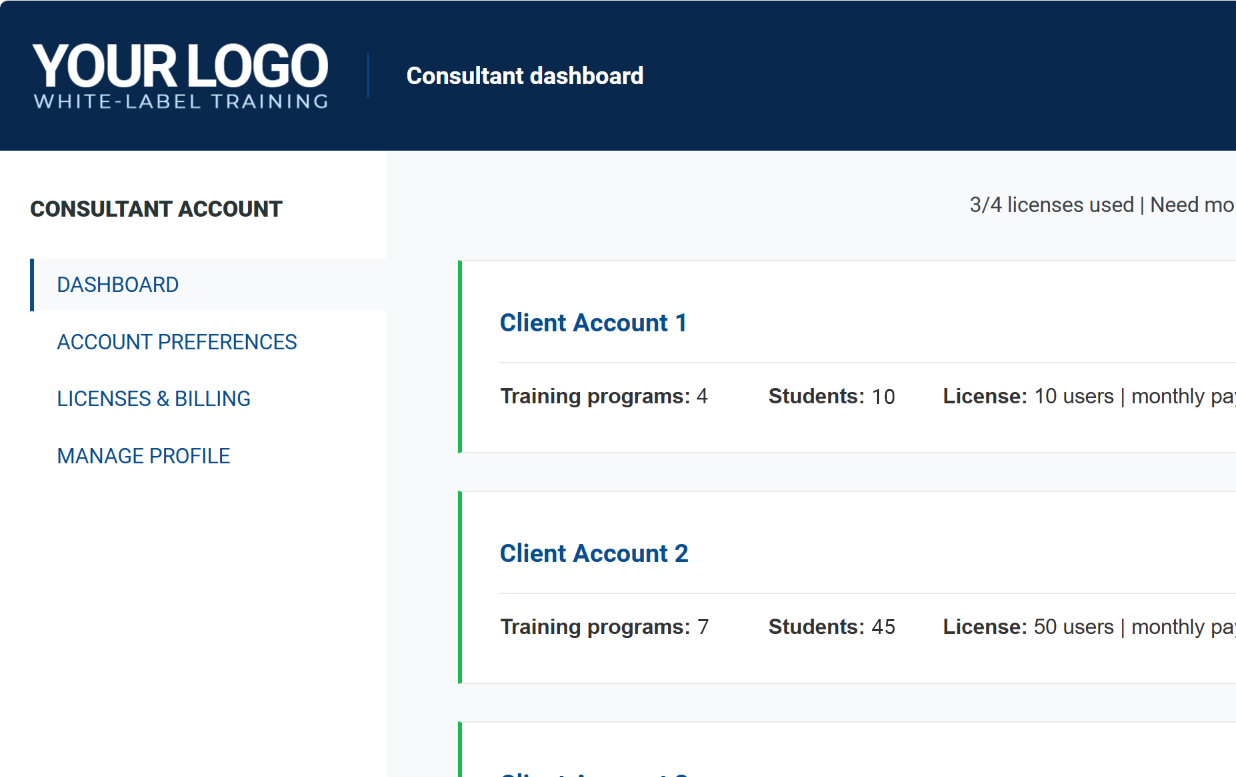
White-label platform for consultants
Monthly plan 10 users included
€14
/ month
$15
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
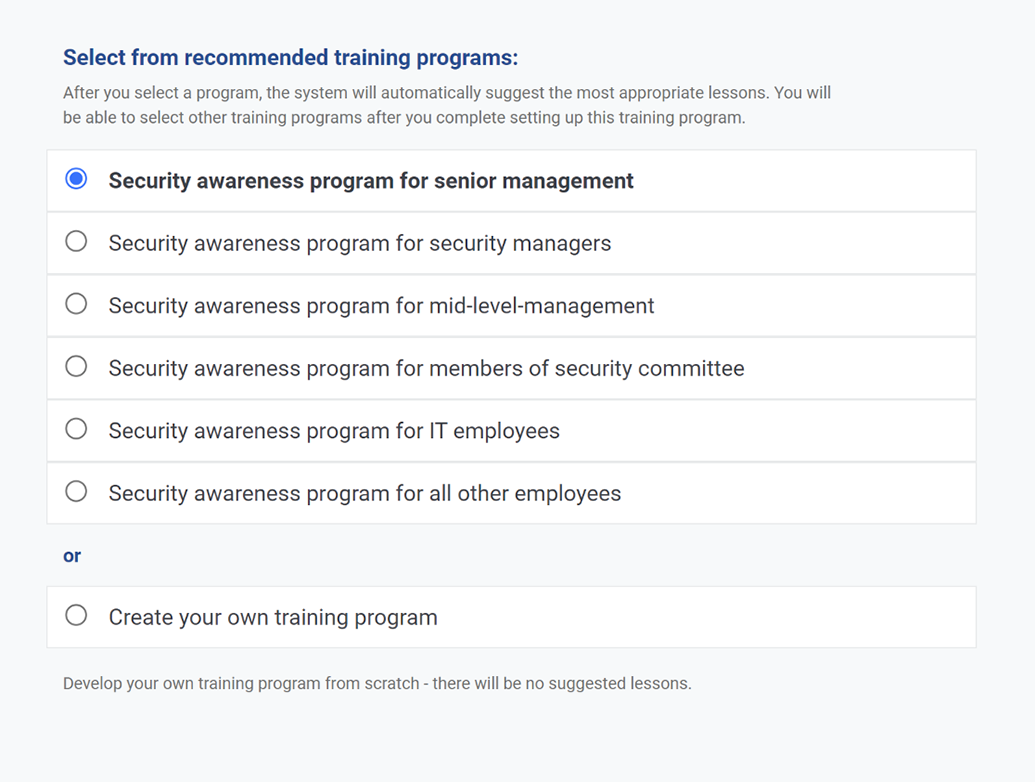
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 25 users included
€28
/ month
$29
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 50 users included
€56
/ month
$59
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 100 users included
€95
/ month
$99
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 200 users included
€189
/ month
$199
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 300 users included
€285
/ month
$299
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 400 users included
€380
/ month
$399
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 500 users included
€475
/ month
$499
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available only in yearly plan)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 10 users included
€154
/ year
$162
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 25 users included
€298
/ year
$313
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 50 users included
€605
/ year
$637
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 100 users included
€1016
/ year
$1069
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
1 video per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 200 users included
€2042
/ year
$2149
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
2 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 300 users included
€3068
/ year
$3229
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
3 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 400 users included
€4094
/ year
$4309
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
4 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 500 users included
€5120
/ year
$5389
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, or GDPR, in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in Croatian, French, Dutch, German, Italian, and Spanish.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
5 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
1 training per year
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Contact us for pricing
Custom number of users
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
For all company sizes, all industries
Frequently Asked Questions
What is the Company Training Academy?
The Company Training Academy is a company-wide cybersecurity training platform that enables you to configure various training and awareness programs for your entire workforce for, e.g., NIS2, DORA, ISO 27001, GDPR, security awareness, etc.
How long does it take to set up company-wide training and awareness?
Opening a client account takes less than a minute. The wizard will then guide you through the process of setting up your first training and awareness program, which usually takes 5–10 minutes.
How does the free trial work?
During the 14-day free trial, you will get access to all training & awareness videos, but you will be limited to 10 users. Some more advanced features will be accessible when you upgrade your account. No credit card required.
What forms of payment do you accept?
We accept payment via any major credit or debit card; for a larger number of users, you can pay via wire transfer from your bank account.
How does the Company Training Academy compare to Advisera’s courses?
Advisera’s courses are intended for individuals who want to get in-depth knowledge about a particular framework, while the Company Training Academy is intended for companies that want to automate training and awareness for all of their employees, and track their progress.
Which standards and regulations are covered in the Company Training Academy videos?
Currently, the videos cover NIS2, DORA, ISO 27001, GDPR, and cybersecurity awareness training.
We’re working on adding videos for other standards and regulations.
Are videos available in languages other than English?
NIS2 and cybersecurity awareness videos are also available in French, Dutch, Croatian, German, Italian, and Spanish. We are working on adding more languages – contact us to learn about available languages.
Can we use these videos in our own Learning Management System (LMS)?
Yes. Our training is available as SCORM packages, including videos, quizzes, and progress tracking, for easy integration into your Learning Management System (LMS) – contact us to request the SCORM packages.
Is there a time limit for attending the training?
No, your users can spend as much time as they like attending the lessons, as long as your subscription is active.
What will the users need to access the lessons?
Your users can access the lessons using PC, Mac, or mobile devices, using any major browser (e.g., Chrome, Mozilla, Edge, Safari); a broadband Internet link will also be needed.
What is the format of the training, and how long does it take?
The lessons are a combination of video lectures, quizzes, and test questions. The average time needed per lesson is between 5 and 10 minutes. You can configure your training program to include only a couple of lessons, or several dozen lessons.
What prior knowledge is needed to attend the training?
None. The lessons are created in such a way that a beginner can easily understand them. They are very easy to follow for any type of employees — senior or mid-level management, non-IT employees, tech people, etc.
How can I upgrade my account if I need more users?
Simply click the purchase button for the required number of users in the pricing table, and, after the payment is processed, your Company Training Academy will be upgraded automatically.
Please make sure you use the same email address that you use for your existing account, because it is the only way this process can be done automatically. If you decide to make the purchase with a different email address, make sure you contact our support at support@advisera.com so we can upgrade your account manually.
Is it necessary to purchase training and awareness certificates?
No — you can use a Company Training Academy without purchasing certificates.
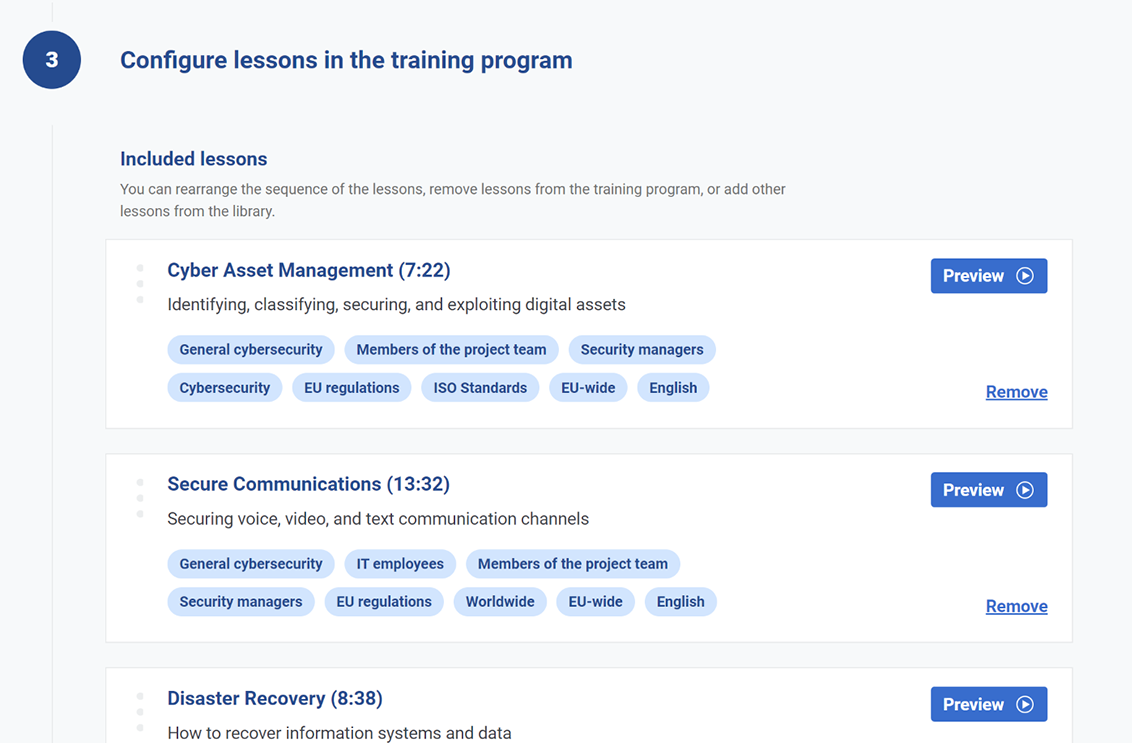
There are so many videos — how will I find what is the most appropriate for us?
The Company Training Academy will suggest the most appropriate videos based on the framework you’re interested in (e.g., NIS2), and based on your audience (e.g., senior management).
Further, you can filter all the videos in the Library by country, language, relevant clauses and articles of the framework, and other criteria.
