Updated: January 04, 2023, according to ISO 27001:2022 revision.
Unfortunately, if you already developed a fixed asset register, it is not going to be enough to be compliant with ISO 27001 – the concept of asset inventory (sometimes called the asset register) in information security is quite different from the concept of the fixed asset register in accounting. Here is ISO 27001 asset management shortly explained.
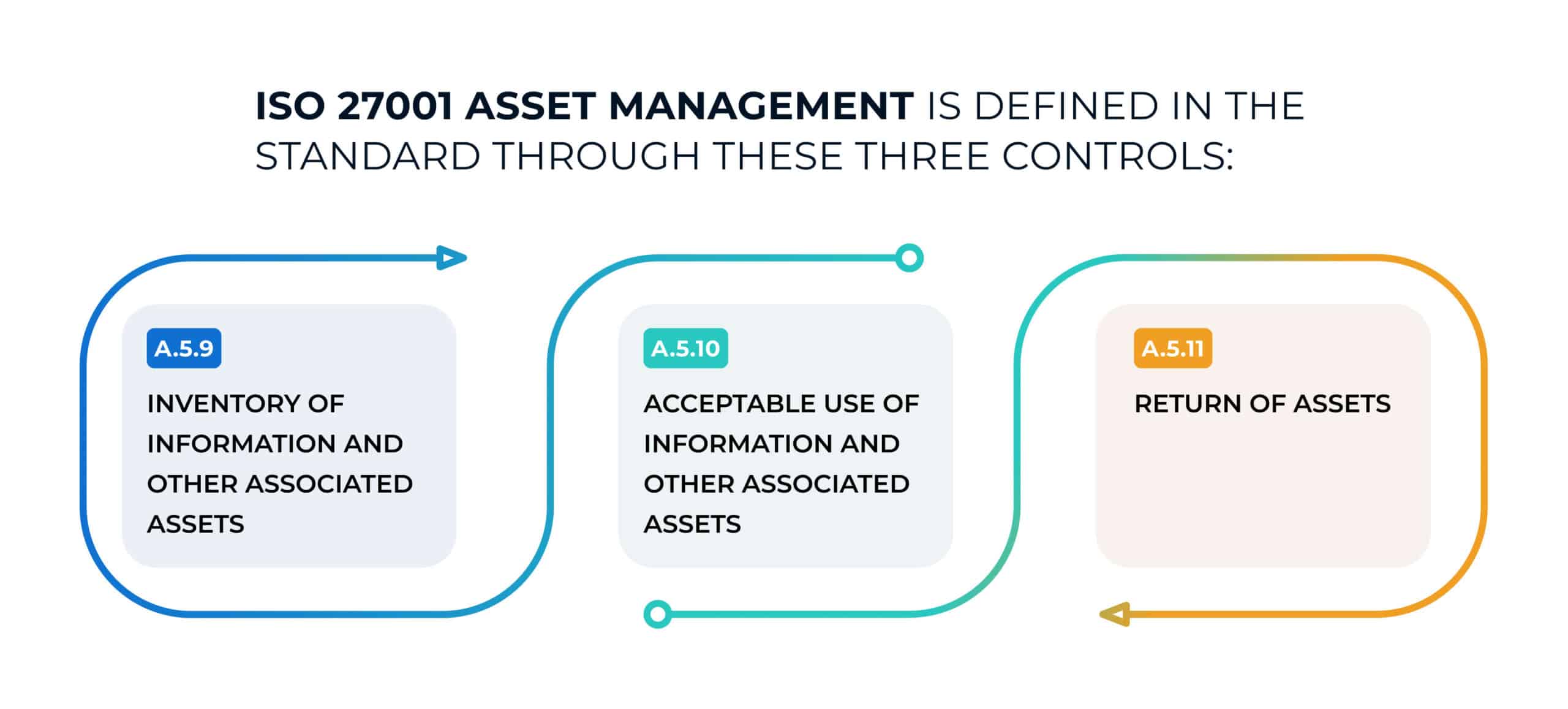
- A.5.9 – Inventory of information and other associated assets
- A.5.10 – Acceptable use of information and other associated assets
- A.5.11 – Return of assets
What are assets according to ISO 27001?
First, let’s clarify what assets means in the context of ISO 27001 – strangely enough, neither the 2022 revision of ISO/IEC 27001, nor the 2018 revision of ISO/IEC 27000, gives a definition of assets, but the 2005 revision of ISO/IEC 27001 defines an asset as “anything that has value to the organization.”
Since ISO 27001 focuses on preservation of confidentiality, integrity and availability of information, this means that assets can be:
- Hardware – e.g., laptops, servers, printers, but also mobile phones or USB memory sticks.
- Software – not only the purchased software, but also freeware.
- Information – not only in electronic media (databases, files in PDF, Word, Excel, and other formats), but also in paper and other forms.
- Infrastructure – e.g., offices, electricity, air conditioning – because those assets can cause lack of availability of information.
- People are also considered assets because they also have lots of information in their heads, which is very often not available in other forms.
- Outsourced services – e.g., legal services or cleaning services, but also online services like Dropbox or Gmail – it is true that these are not assets in the pure sense of the word, but such services need to be controlled very similarly to assets, so they are very often included in the asset management.
What is ISO 27001 asset management?
Although ISO 27001 does not have a formal definition for asset management, it has three specific controls in its Annex A to ensure proper asset management (which can be understood in an ISO 27001 context as ensuring the asset protection while the asset is important to the organization):
- A.5.9 – Inventory of information and other associated assets: all information and related assets need to be identified and have an owner responsible for protecting the confidentiality, integrity, and availability of the information. Asset ownership is one of the fundamental concepts in ISO 27001.
- A.5.10 – Acceptable use of information and other associated assets: rules for proper use of assets need to be defined, documented, and implemented.
- A.5.11 – Return of assets: upon termination of business relations, all users in possession of information assets need to return them to the organization.
Why are assets important for information security management?
There are two reasons why managing assets is important:
1) Assets are usually used to perform the risk assessment – although not mandatory by ISO 27001:2022, assets are usually the key element of identifying risks, together with threats and vulnerabilities. See also ISO 27001 Risk Assessment, Treatment, & Management: The Complete Guide.
2) If the organization doesn’t know which assets it possesses, who is responsible for them, and how they must be handled, chaos would ensue.
This is why ISO 27001:2022 requires asset management.
How to build an asset inventory?
If you didn’t develop your asset inventory previously, the easiest way to build it is during the initial risk assessment process (if you have chosen the asset-based risk assessment methodology), because this is when all the assets need to be identified, together with their owners.
The best way to build asset inventory is to interview the head of each department, and list all the assets a department uses. The easiest is the “describe-what-you-see” technique – basically, ask this person e.g., to list all the software that he or she sees that are installed on the computer, all the documents in their folders and file cabinets, all the people working in the department, all the equipment seen in their offices, etc.
Of course, if you already do have some existing asset inventories (e.g., fixed asset register, employee list, licensed software list, etc.), then you don’t have to duplicate those lists – the best would be to refer to your other lists from your information security Asset register.
ISO 27001 does not prescribe which details must be listed in the asset inventory – you can list only the asset name and its owner, but you can also add some other useful information, like asset category, its location, some notes, etc.
Building the asset register is usually done by the person who coordinates the ISO 27001 implementation project – in most cases, this is the Chief Information Security Officer, and this person collects all the information and makes sure that the inventory is updated.
Who should be the asset owner?
The owner is normally a person who operates the asset and who makes sure the information related to this asset is protected. For instance, an owner of a server can be the system administrator, and the owner of a file can be the person who has created this file; for the employees, the owner is usually the person who is their direct supervisor.
For similar assets used by many people (such as laptops or mobile phones), you can define that an asset owner is the person using the asset, and if you have a single asset used by many people (e.g., an ERP software), then an asset owner can be a member of the board who has the responsibility throughout the whole organization – in this case of ERP, this could be the Chief Information Officer.
Read also Risk owners vs. asset owners in ISO 27001.
So, the point is – building an asset register compliant with ISO 27001 can seem like a bureaucratic job with not much practical use, but the truth is that listing assets helps clarify what is it valuable in your company and who is responsible for it. And, without knowing what you have and who is in charge, don’t even think that you will be able to protect your information.
To see how to use the ISO 27001 risk register with catalogs of assets, threats, and vulnerabilities, and to get automated suggestions on how they are related, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.

 Dejan Kosutic
Dejan Kosutic