Rhand Leal
Rhand Leal
December 3, 2018
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Training products for Artificial Intelligence Management Systems (AIMS) and AI governance according to the ISO 42001 standard.
Accredited courses for individuals, consultants, and AI professionals who want the highest-quality training and certification in AI governance and compliance.
Train your key people on ISO 42001 requirements and provide company-wide AI governance training so employees learn how to use AI responsibly and in compliance with your policies.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Rhand Leal
Rhand Leal
Update 2022-04-25.
No environment can be 100% secure. Problems (which can be broadly described as “occurrences” or “deviations”) will happen, but not all problems need to be treated the same way, and this can have a significant impact on the effort, and costs, of security management.
This article will present three concepts used by ISO 27001, the leading standard for information security management, that can help companies handle security events, security incidents, and non-compliances in a more efficient way. We’ll learn about the definitions of these concepts and how to differentiate among them.
For the purposes of ISO 27001, the ISO 27000 standard, which defines the vocabulary for ISO information security management, uses the following concepts.
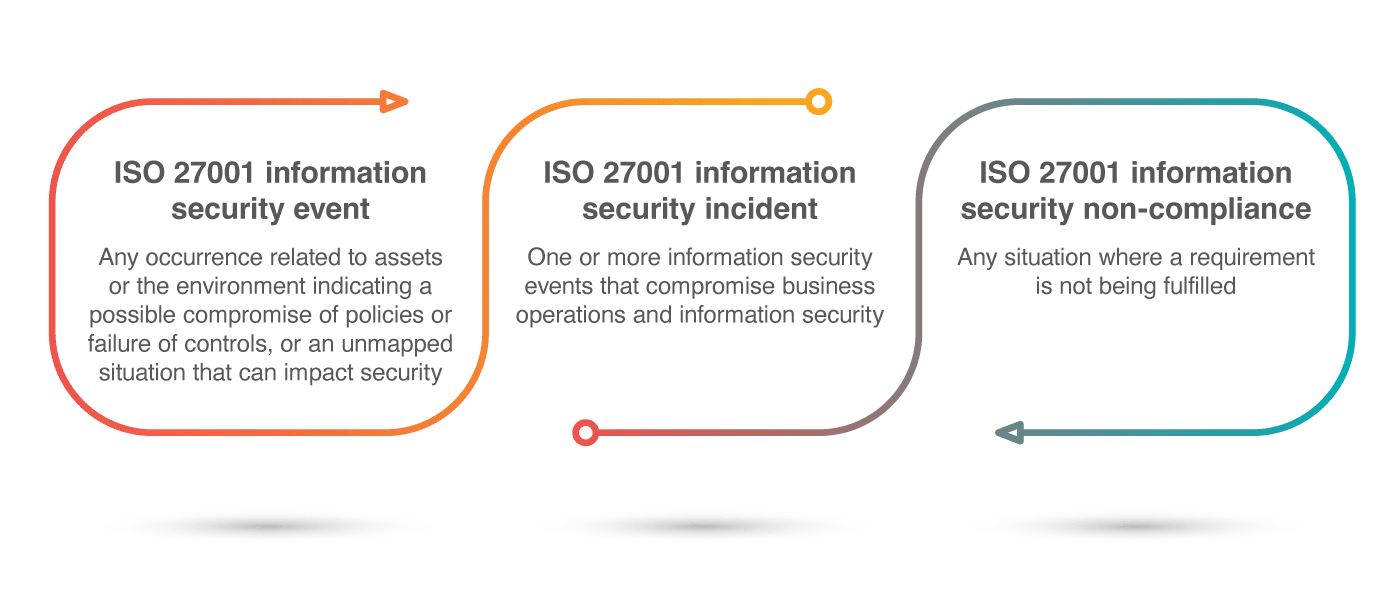
An information security event is any occurrence related to assets or the environment indicating a possible compromise of policies or failure of controls, or an unmapped situation that can impact security.
It is also a change in the normal or expected behavior of a system, network, or service. An event doesn’t always have to cause an incident. There may be many attacks to your network blocked by your firewall or antivirus, which are all events, but do not harm your system or data; so, they are not incidents.
An information security incident is one or more information security events that compromise business operations and information security.
An information security incident is caused by event that has the potential to affect the confidentiality, integrity, or availability of information. Theft or loss of equipment, such as a company laptop containing classified or sensitive information stolen from bag or forgotten at an airport lounge, is an example of an information security incident.
Information security non-compliance is any situation where a requirement is not being fulfilled.
For example, the Access Control Policy requires access for new employees to be approved by the head of the department, whereas the access is approved by the system administrator.
To differentiate among these concepts, and to learn to recognize each, note that:
It is important to note that events and incidents may also fall under information security non-compliance at the same time. For example, in the previous example of a security event, let’s imagine that surveillance cameras covering the area are installed as a security measure. If the suspicious person was identified by an employee report instead of the cameras’ operator (e.g., because he was not paying attention), then this is a non-compliance regarding the cameras’ operation, even if there is no negative impact on the business or its information. In the example of the security incident, if the cause was a change not being performed according to the Change Control Policy, then this is also a non-compliance together with the incident.
Let’s see the differences between these three concepts using an example of a hacker attack:
Understanding the abovementioned concepts and their differences is paramount to increase efficiency in the handling of security occurrences.
The different concepts of events, incidents, and non-compliances also mean that treating them must be done in different ways in order to prevent wasted resources, or the use of insufficient measures, leading to a recurrence of the unwanted situations. Here is how you can approach them:
Events: these just need to be recorded for future analysis. When performing the analysis (normally during monitoring and measurement of processes), if the quantity of similar occurrences in the period is significant, there may be a need to review the risk assessment, policies, or procedures. For more information, please read How to perform monitoring and measurement in ISO 27001.
Incidents: because they affect the business or its information, incidents require immediate action to contain the impact (if an incident is still happening after identification), and to recover normal operational conditions. Like events, they need to be recorded for future analysis during the monitoring and measurement of processes. For detailed information, please read How to handle incidents according to ISO 27001 A.16 and Logging and monitoring according to ISO 27001 A.12.4.
Non-compliance: like other management system standards, ISO 27001 requires action to control and correct any non-compliance, as well as to handle its consequences. Additionally, an organization has to evaluate the need to eliminate root causes in order to prevent recurrence. In cases where actions to eliminate root causes are taken, they must be reviewed for their effectiveness. For more information, see Practical use of corrective actions for ISO 27001 and ISO 22301.
Most organizations address incidents and non-compliance with reactive actions, and the key to increase the effectiveness of occurrence handling is to work in a preventive way, periodically evaluating the events log and root causes of non-compliances to identify patterns that may lead to new incidents and their related non-compliances. This way, you will be decreasing the probability of new incidents happening and of having to allocate extra resources to handle their consequences.
An additional approach is to work on policies, procedures, and controls so they are not excessively strict, in this way decreasing the occurrence of non-compliance. In this case, you have to balance the risk level with the rigor of policies, procedures, and controls. For more information, please read How detailed should the ISO 27001 documents be?
Operational efficiency is paramount for any businesses. Often, information security is seen as an expense, so every effort to decrease not only costs related to incidents, but also to handling security occurrences in general, will be seen as a proactive measure.
It’s important for a company to determine its compliance obligations and to have its own threshold for defining if something is an event or an incident.
By using the ISO 27001 framework and its related concepts to address information security occurrences, an organization can minimize its efforts and costs to keep the business running with acceptable levels of risks to its information and that of its customers.
To help you automate incident management according to ISO 27001, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

Rhand Leal has more than 15 years of experience in information security, and for six years he continuously maintained а certified Information Security Management System based on ISO 27001.
Rhand holds an MBA in Business Management from Fundação Getúlio Vargas. Among his certifications are ISO 27001 Lead Auditor, ISO 9001 Lead Auditor, Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), and others. He is a member of the ISACA Brasília Chapter.

Tolga Aktaş has been working in various disciplines of management systems for more than 15 years. Tolga is an accredited lead auditor for the ISO 9001, 14001, 18295, 22301, 27001, 27701, 37001, and 55001 standards and has conducted audits as a freelancer for internationally accredited conformity assessment companies. He is also an accredited lead auditor trainer for ISO 22301, 27001, and 27701. He conducts workshops and webinars, and provides consultancy services on management systems to organizations mainly in Turkey, the UK, the EU, Qatar, UAE, Germany, and Japan. Tolga holds a Master of Business Administration degree.

You may unsubscribe at any time. For more information, please see our privacy notice.