Most of the information security/business continuity practitioners I speak with have the same problem: the employees in their companies don’t take them seriously – not only the top managers, but also their peers.
This is due to the fact that the employees usually do not understand what information security or business continuity is all about – in other words, you may have perfect policies and procedures, but simply pushing those to your internal email list won’t help. You need to explain to your colleagues why information security and business continuity are needed, and how to perform certain tasks – that’s the main purpose of ISO 27001 awareness and training.
- Define which knowledge and skills are required.
- Perform trainings to reach the desired level.
- Measure whether each individual has achieved the desired level.
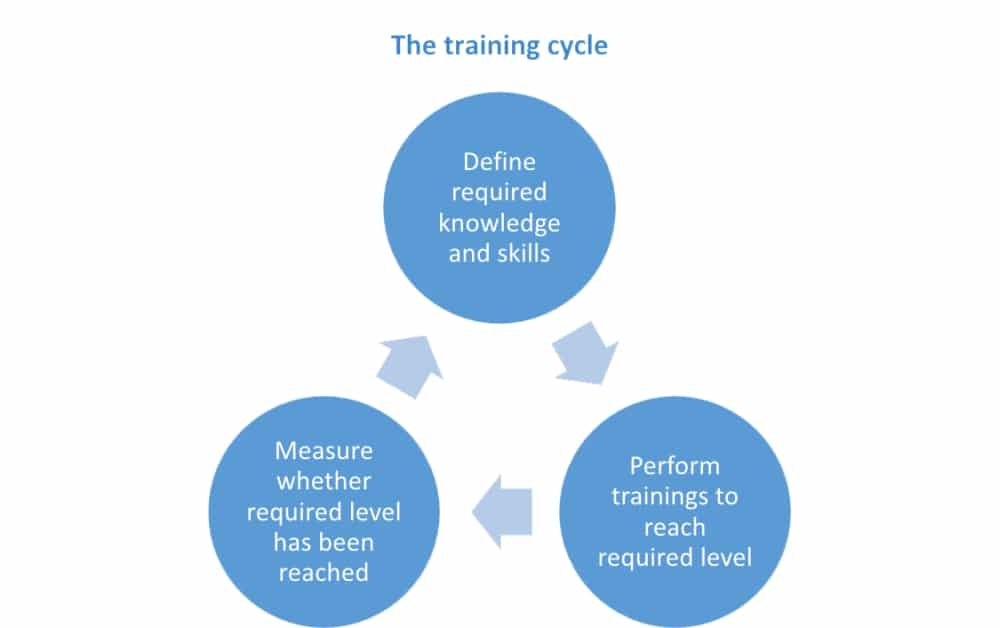
The training cycle
Both ISO 27001 and ISO 22301 require you to deal with training in a systematic manner, i.e. to perform these steps:
- Define which knowledge and skills are required for particular personnel who have a role in your information security management system (ISMS) or business continuity management system (BCMS) – basically, you need to go through every ISMS or BCMS document and see what knowledge and skills are required of every responsible person mentioned in the document.
- Perform trainings to reach the desired level of knowledge and skills – see below for methods.
- Measure whether each individual has achieved the desired level of knowledge and skills – through testing, interviews, etc. – once you know where the gaps are, you can start again with step #1.
And this is something that needs to be done continuously – either by the CISO / business continuity coordinator, or by the HR department.
Methods of training
Very often, the trainings are planned via the Training plan – for example, you can plan for the following:
- Courses – see this article for more information: How to learn about ISO 27001 .
- Reading literature – there are many information security and business continuity books available, as well as magazines.
- Participating in expert forums on the Internet – in some of those you can get very concrete answers to your questions – for example, Expert Advice Community or ISO 27001 security.
- In-house trainings – delivered either by in-house experts, or by hiring consultants, certification bodies or similar.
Methods of awareness-raising
As opposed to trainings, which give an answer to the question “How?”, awareness must give an answer to the question “Why?” – that is, explain to your employees why they should accept information security or business continuity.
There are many methods you can use, for example:
- Include employees in documentation development – before you publish the documents, ask your employees to give their inputs (see also: Seven steps for implementing policies and procedures).
- Presentations – organize shorter meetings where you can explain what new policies and procedures are being published, ask your employees for opinions about them, clarify any misunderstandings.
- Articles on your intranet or newsletter – simple stories (with as many examples as possible) that can help employees understand why information security / business continuity are important.
- Discussions through internal forums – you can initiate and participate in concrete questions (and myths) arising from information security / business continuity.
- E-learning – you can create short online trainings that explain the significance of these topics, as well as train your employees.
- Videos – they are a very powerful presentation method – you can distribute them via email, through the intranet, etc.
- Occasional messages (via email or via your intranet) – can be used not only to distribute videos, but also to send relevant news and tips for business continuity.
- Gatherings – use some regular meetings that are organized in your company – e.g., parties, anniversaries, etc. to briefly present what you are doing and how it affects your colleagues.
- And, above all – day-to-day in-person communication – everywhere you go, whomever you speak to – you have to sell the idea of information security / business continuity.
No matter which of these methods you use, the point is that you do them systematically – again, you should prepare some kind of a plan where you should define which of these methods you will perform, and how often.
The implementation myth
So, as I emphasized in this article: The documentation myth – Why the templates are not enough?, simply writing the policies and procedures won’t be enough – you need to use awareness and trainings as a helping tool to enable the documentation to be implemented.
However, the timing here is also crucial: many companies make the mistake of publishing all of their documents at once. For example, if you publish 30 policies and procedures at the same time, then unfortunately, not even the best awareness programs can help you – your employees will (very correctly) start to think of your information security / business continuity as overkill.
Therefore, you have to publish your documentation gradually – the speed of publishing your new documents must be not be the speed of developing them, but the speed by which your employees will be able to accept them via your ISO 27001 awareness and training programs.
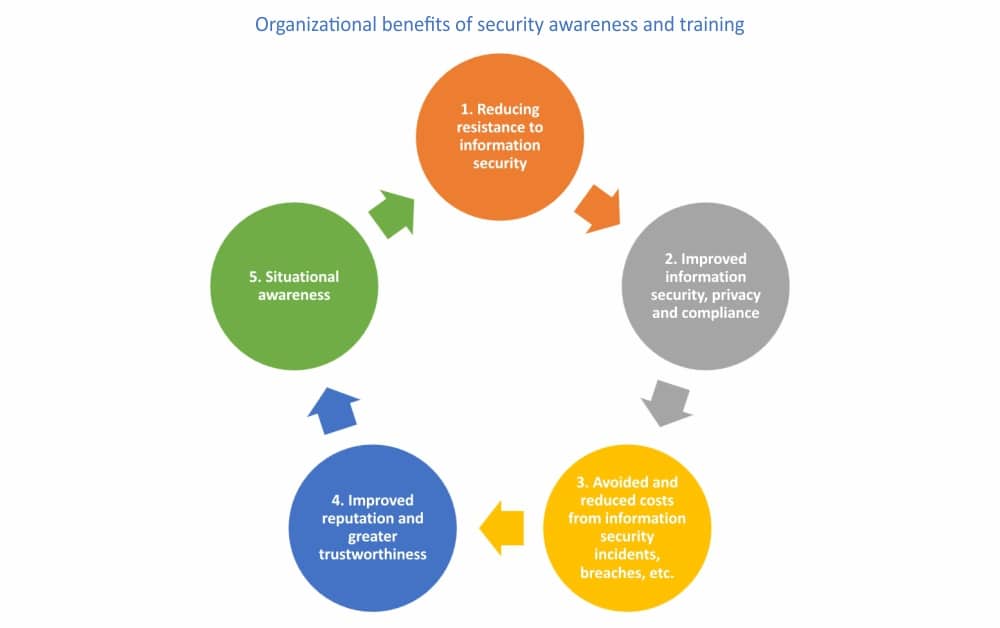
Benefits of security awareness training for companies
Security awareness, and especially training, are not (always) free though, so how do we justify the expense? Let’s examine the five potential business benefits.
- Reducing resistance to information security
Given sufficient awareness and/or training, employees make better, more effective, and more efficient use of security controls. For starters, they appreciate that the controls are there for good reason; hence, they are less likely to ignore, bypass, or disable them. Understanding why we need long passwords, for instance, and how to choose strong, yet memorable passwords or passphrases, makes it easier to be secure. Employees refusing to disclose or share their passwords is another control bolstered through awareness and training. - Improved information security, privacy, and compliance
The most immediate benefit of awareness and training arises from improvements to the organization’s information security arrangements. A clear desk policy, for instance, is almost worthless if employees don’t know about it, don’t care, and can’t be bothered to comply. Awareness to the rescue! The mere existence of the policy is, in itself, a sign that management appreciates the need, while its clarity, focus, and motivational effectiveness depend on the author/s being sufficiently clued up. As an integral part of an organization-wide approach to information risk management, security awareness and training enable all the other security controls, and support the achievement of a wide range of business objectives – including compliance with privacy, accounting, governance, and other laws and regulations. - Avoided or reduced costs from information security incidents, breaches, etc.
Compared to the average organization, a security-aware workforce, supported and guided by highly trained security professionals, is less likely to suffer information security incidents, privacy breaches, unplanned downtime, and so forth. Employees who know what to look out for are less likely to fall for obvious scams or to ignore the early signs of trouble. They are the equivalent of skilled drivers, being extra cautious when appropriate and able to make good progress when the road conditions are favorable.What’s more, any incidents that do occur are likely to be shorter and more limited due to employees’ spotting and reacting appropriately. Incident response can’t start until an incident is recognized and reported, both of which depend on employees knowing what to do, without delay. - Improved reputation and greater trustworthiness
If a majority of the workforce is security-aware, outsiders and visitors perceive an organization that clearly takes security and privacy seriously. From the moment someone arrives at the premises or visits the corporate website, there are clues – some obvious, such as warning signs and security certificates, and others that are more subtle, such as efficiently following structured processes. Differences in how people and organizations interact affect the extent to which they are willing to depend on each other. Trust is a major factor in commerce, and a significant part of an organization’s reputation and brands. Consider the differences between shopping at a temporary street market compared to, say, a department store, or a backstreet car lot compared to a major dealer. In business, impressions matter! - Situational awareness
“Situational awareness” is almost a sixth sense. It’s hard to explain precisely why an email or phone call “doesn’t seem quite right,” especially as each situation is different; hence, it is impossible to define precise rules on what to look out for. It is true that many phishing emails start with a nonspecific greeting such as “Dear customer,” but some don’t: spear-phishing attacks commonly use the recipient’s name, often with other information intended to give the appearance that the sender is a colleague, acquaintance, or friend. What’s more, that inkling of something wrong achieves nothing unless the employee reacts appropriately, not opening the attachment or clicking the link, for instance, and perhaps seeking help to check out the message.
Better safe than sorry
Besides being a long-term investment in the overall business success, awareness and training are an integral and essential part of any sensible approach to information security. If you are still not convinced of its purpose and value, consider the alternative: sure, the organization won’t have to pay for security awareness materials and training activities, but employees will be naïve, uninformed, and unmotivated. Security controls will be neglected, forgotten, and sometimes disabled or bypassed for the sake of convenience. The organization will appear untrustworthy, its reputation and bottom line both tarnished by incidents and breaches that should have been prevented or mitigated.
See here a series of 25 free security awareness videos that can be easily understood by any employee in your company.

 Dejan Kosutic
Dejan Kosutic